Quantum cryptography is a relatively new field that has the potential to revolutionize the way we communicate and secure our information. It is based on the principles of quantum mechanics, and it offers a level of security that is impossible to achieve with classical cryptography. Quantum cryptography has already been successfully implemented in various industries, including banking, healthcare, and government. In this post, we will explore the basics of quantum cryptography and discuss some real-life examples of how it is being used to secure information. We will also discuss some of the challenges associated with implementing quantum cryptography, and what the future holds for this emerging field. So, let’s dive into the world of quantum cryptography and unlock its secrets!
Introduction to Quantum Cryptography and its significance
In an era where data security is of paramount importance, quantum cryptography emerges as a groundbreaking solution that promises unparalleled protection against cyber threats. But what exactly is quantum cryptography, and why is it so significant in today’s digital landscape?
At its core, quantum cryptography is a branch of cryptography that leverages the principles of quantum mechanics to secure the transmission of information. Unlike traditional cryptographic methods that rely on complex mathematical algorithms, quantum cryptography utilizes the fundamental properties of quantum physics to ensure the utmost security.
One of the most intriguing aspects of quantum cryptography is its reliance on the phenomenon of quantum entanglement. This phenomenon allows two particles to become intrinsically linked, regardless of the distance between them. Any change in one particle instantaneously affects the other, enabling the creation of an unbreakable bond.
The significance of quantum cryptography lies in its ability to achieve secure communication channels that are impervious to hacking attempts. Traditional cryptographic methods, while effective, are vulnerable to increasingly sophisticated cyber attacks, such as brute force attacks and quantum computing-powered decryption. Quantum cryptography, on the other hand, offers a revolutionary approach that can provide absolute security, even against attacks from quantum computers.
To illustrate the real-life impact of quantum cryptography, let’s consider an example. Imagine a confidential message being transmitted between two parties over a standard internet connection. In this scenario, the message is susceptible to interception and decryption by malicious actors. However, by employing quantum cryptography protocols, the information can be encoded using quantum bits, or qubits, which are immune to eavesdropping attempts. Any attempt to intercept the qubits would disrupt their delicate quantum state, immediately alerting the communicating parties to the presence of an intruder.
The potential applications of quantum cryptography are vast and far-reaching. From securing classified government communications to safeguarding financial transactions and protecting personal data, the implications are profound. By harnessing the power of quantum mechanics, this cutting-edge technology has the potential to revolutionize the field of cybersecurity and transform the way we transmit and protect sensitive information.
In the following sections, we will delve deeper into the principles and mechanisms behind quantum cryptography, exploring its various protocols and algorithms. Through real-life examples and case studies, we will uncover the secrets of this fascinating field and shed light on its immense potential for a secure digital future. Stay tuned as we embark on this captivating journey into the world of quantum cryptography.
Understanding the basics: The Principles of Quantum Mechanics
To truly delve into the fascinating world of quantum cryptography, it is essential to understand the basics of quantum mechanics. While the subject itself can be complex and mind-boggling, we will simplify it here to provide a foundation for exploring quantum cryptography.
At its core, quantum mechanics is a branch of physics that examines the behavior of matter and energy at the smallest scales. It challenges our intuition and traditional understanding of how the world works, as it is governed by principles quite different from classical physics.
One of the fundamental principles of quantum mechanics is superposition. This concept states that particles can exist in multiple states or positions simultaneously until they are observed or measured. This means that a particle can exist in two or more states, known as quantum states, at the same time, and it is only upon observation that it “collapses” into a single state.
Another principle is entanglement, which involves the strong correlation between particles, even when they are physically separated. When two particles become entangled, their properties become intertwined. Any change in one particle’s properties instantly affects the other, regardless of the distance between them. This phenomenon is often referred to as “spooky action at a distance” and remains one of the most puzzling aspects of quantum mechanics.
Quantum mechanics also introduces the concept of uncertainty, as described by Heisenberg’s uncertainty principle. This principle states that there is an inherent limit to the precision with which certain pairs of physical properties, such as position and momentum, can be known simultaneously. This notion challenges the classical idea of precise measurements and introduces a level of unpredictability at the quantum level.
Understanding these basic principles of quantum mechanics sets the stage for exploring how they can be harnessed for secure communication in quantum cryptography. By leveraging the unique properties of quantum mechanics, such as superposition and entanglement, researchers have developed cryptographic protocols that offer unprecedented levels of security.
In the following sections, we will delve into real-life examples of how quantum cryptography is being applied to protect sensitive information in various domains, including banking, government communications, and data transmission. By unlocking the secrets of quantum mechanics, we can unlock the potential of quantum cryptography and pave the way for a new era of secure communication.
The Concept of Quantum Key Distribution (QKD)
Quantum key distribution (QKD) is a groundbreaking concept that lies at the core of quantum cryptography. It utilizes the principles of quantum mechanics to establish a secure channel for transmitting cryptographic keys between two parties. Unlike traditional cryptographic methods that rely on complex algorithms, QKD harnesses the unique properties of quantum physics to ensure unparalleled security.
At its essence, QKD involves the transmission of quantum particles, typically photons, over a communication channel. These particles, carrying quantum information, are used to generate a random sequence of bits that form the cryptographic key. The remarkable aspect of QKD is that any attempt to intercept or eavesdrop on this transmission would disturb the delicate quantum state, making it immediately detectable.
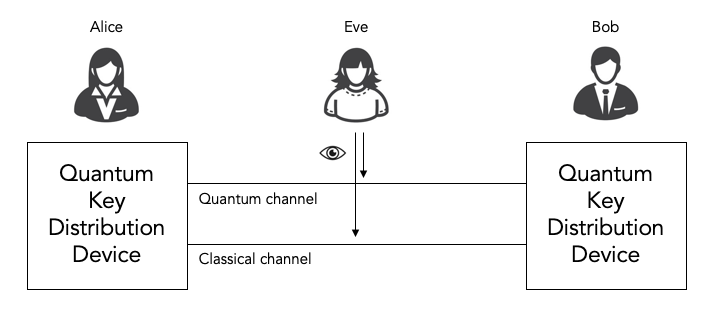
To understand this concept better, let’s consider a real-life example. Imagine two individuals, Alice and Bob, who want to establish a secure communication channel using QKD. They each possess a device capable of generating and receiving quantum particles, such as photons.
Alice begins by randomly encoding each photon in one of two polarizations, representing binary 0 and 1. She then sends these photons to Bob through a dedicated quantum channel. Meanwhile, Bob uses a measurement device to detect the polarization of each received photon.
The key idea behind QKD is that any attempt to measure or intercept the photons will inevitably disturb their quantum state. Therefore, if an eavesdropper, let’s call her Eve, tries to gain information about the transmitted key, her presence will be detected. This is due to the laws of quantum mechanics, which dictate that the act of observation alters the observed system.
Upon receiving the photons, Bob communicates with Alice over a separate classical channel to compare the polarizations of the photons he measured. They discard any data where the polarizations do not match, as those could have been compromised by Eve’s interference. Through a process called privacy amplification, they then extract a final shared key that is guaranteed to be secure.
The beauty of QKD lies in its ability to offer information-theoretic security, meaning that the security of the key is based on fundamental physical principles rather than computational assumptions. This provides an unprecedented level of security against hacking attempts, including future advances in computing power.
In conclusion, the concept of quantum key distribution (QKD) revolutionizes the field of cryptography by leveraging the laws of quantum mechanics to establish secure communication channels. Real-life examples, such as the transmission of quantum particles between Alice and Bob, illustrate the remarkable security offered by QKD. By understanding and exploring this concept further, we can unlock the secrets of quantum cryptography and pave the way for a more secure digital future.
How Quantum Cryptography ensures secure communication
Quantum cryptography is a fascinating and cutting-edge field that revolutionizes the way we think about secure communication. Unlike traditional cryptographic methods that rely on mathematical algorithms, quantum cryptography leverages the principles of quantum mechanics to ensure secure and unbreakable communication channels.
At the heart of quantum cryptography is the concept of quantum key distribution (QKD), which allows two parties to establish a shared secret key without the risk of interception or eavesdropping. This key serves as the foundation for encrypting and decrypting messages, guaranteeing confidentiality and integrity.
One of the most intriguing aspects of quantum cryptography is the phenomenon of quantum entanglement. In simple terms, entanglement refers to the interconnectivity between quantum particles, where the state of one particle directly influences the state of another, regardless of the distance separating them. This property allows for the creation of secure communication channels that are inherently resistant to hacking attempts.
To illustrate how quantum cryptography works in practice, let’s consider a scenario where Alice wants to securely communicate with Bob. They use a quantum key distribution protocol that involves sending a series of quantum particles, such as photons, over a dedicated quantum channel.
Alice generates a random sequence of photons, each with a specific polarization state. She then sends these photons to Bob, who measures their polarization using specialized equipment. Due to the principles of quantum mechanics, any attempt to intercept or observe these photons will inevitably disturb their quantum state, alerting Alice and Bob to the presence of an eavesdropper.
After the transmission, Alice and Bob exchange information about the measurement results over a classical channel. By comparing a subset of their results, they can detect any discrepancies caused by potential eavesdroppers. If the comparison reveals no interference, they can safely assume that the channel is secure and use the shared key to encrypt their subsequent communication.
Quantum cryptography offers an unprecedented level of security, as it is based on the fundamental laws of physics rather than computational complexity. While it may still be in its early stages of development and implementation, the potential applications of quantum cryptography are vast, ranging from secure financial transactions to military communications.
In conclusion, quantum cryptography harnesses the peculiar properties of quantum mechanics to provide a secure foundation for communication. By leveraging quantum key distribution and the principles of entanglement, it ensures that messages remain confidential and protected from malicious actors. As scientists and researchers continue to explore this field, we can expect quantum cryptography to play an increasingly vital role in safeguarding our digital interactions in the future.
Real-life examples of Quantum Cryptography in action
Quantum cryptography may seem like a concept straight out of science fiction, but it is a rapidly developing field with real-life applications. Let’s explore some fascinating examples of how quantum cryptography is being utilized in various industries.
One compelling use case of quantum cryptography is secure communication. Traditional encryption methods are based on mathematical algorithms, which can be vulnerable to advanced computing power. Quantum cryptography, on the other hand, leverages the principles of quantum mechanics to provide unbreakable encryption.
In the financial sector, quantum cryptography is being employed to secure sensitive transactions. For instance, banks are using quantum key distribution (QKD) protocols to establish secure communication channels between branches and customers. This ensures that confidential financial information, such as account details and transaction data, remains protected from potential hackers.
Another area where quantum cryptography is making waves is in the realm of data privacy. With the rise of cloud computing and the increasing volume of data being transmitted and stored online, ensuring the confidentiality of sensitive information has become a critical concern. Quantum cryptography offers a solution by enabling the secure transmission of data over long distances without the risk of interception or tampering.
In the healthcare industry, quantum cryptography is being explored to safeguard patient records and medical data. By implementing quantum-resistant encryption algorithms, healthcare providers can ensure the privacy and integrity of sensitive patient information, preventing unauthorized access and potential breaches.
Beyond traditional applications, quantum cryptography is also being utilized in cutting-edge technologies such as quantum key distribution satellites. These satellites enable secure communication between two distant locations on Earth by distributing encryption keys using quantum properties of entangled particles. This breakthrough technology has the potential to revolutionize secure communication on a global scale.
As quantum cryptography continues to evolve, its applications will likely expand across various sectors, providing enhanced security and privacy in an increasingly interconnected world. The real-life examples mentioned here are just a glimpse of the potential that quantum cryptography holds, and we can expect to witness even more fascinating implementations in the future.
Quantum key distribution protocols

Quantum key distribution (QKD) protocols are at the forefront of quantum cryptography, revolutionizing the way we secure our communications. Unlike classical encryption methods, which rely on mathematical algorithms, QKD leverages the principles of quantum physics to establish secure keys that are virtually uncrackable.
One of the most widely known QKD protocols is the BB84 protocol. Developed by Charles H. Bennett and Gilles Brassard in 1984, the BB84 protocol provides a secure method for distributing cryptographic keys between two parties. It uses the properties of quantum particles, such as photons, to transmit information securely.

In the BB84 protocol, Alice (the sender) and Bob (the receiver) agree on a set of quantum states, typically represented by two orthogonal bases, such as the rectilinear basis (horizontal and vertical polarizations) and the diagonal basis (45-degree and 135-degree polarizations). Alice randomly chooses a basis and encodes her message using quantum states representing the chosen basis. She then sends the encoded quantum states to Bob.
Upon receiving the quantum states, Bob randomly chooses a basis to measure the states. If Bob measures the states in the same basis that Alice used to encode them, he will obtain the correct measurement results. However, if Bob chooses a different basis, he will randomly measure one of the two possible outcomes.
After the transmission, Alice and Bob publicly communicate their chosen bases for each transmission round. They discard the measurement results when their bases do not match and keep the remaining results as the raw key. To establish a secure key, Alice and Bob perform a process called information reconciliation and privacy amplification to correct errors and reduce the amount of information an eavesdropper could potentially possess.
Real-life examples of QKD protocols in action include the SwissQuantum project, which deployed a QKD network between the University of Geneva and the Swiss parliament building. This project demonstrated the practicality and security of using QKD for secure communication over long distances.
QKD protocols have the potential to revolutionize secure communication, providing an unprecedented level of security based on the fundamental principles of quantum physics. As researchers continue to explore and refine these protocols, the future of quantum cryptography holds great promise in ensuring the confidentiality and integrity of our sensitive information.
Quantum encryption and decryption processes
Quantum encryption and decryption processes play a crucial role in the realm of quantum cryptography. Unlike classical encryption methods that rely on mathematical algorithms, quantum encryption utilizes the principles of quantum mechanics to ensure unbreakable security.
In the field of quantum cryptography, two primary processes are involved: quantum key distribution (QKD) and quantum encryption/decryption.
QKD is the cornerstone of quantum cryptography, enabling the secure distribution of cryptographic keys between two parties, often referred to as Alice and Bob. This process leverages the fundamental principles of quantum mechanics to establish a secure communication channel. Quantum particles, such as photons, are used to transmit the cryptographic keys. Any attempt to intercept or eavesdrop on these particles would cause a disturbance, immediately alerting the communicating parties to the presence of an intruder.
Once the cryptographic key is securely distributed through QKD, the quantum encryption and decryption processes come into play. Quantum encryption algorithms use the cryptographic key to transform the plaintext message into an encoded form, often involving complex mathematical operations. This encoded message, known as the ciphertext, is unintelligible without the corresponding decryption key.
On the receiving end, Bob utilizes the quantum decryption process, which employs the same cryptographic key to reverse the encryption and retrieve the original plaintext message. Thanks to the principles of quantum mechanics, any attempt to intercept or tamper with the encrypted message would introduce errors that can be detected by Alice and Bob as a sign of potential eavesdropping.
To better understand the power of quantum encryption and decryption, let’s consider an example. Imagine Alice wants to send a confidential message to Bob over an insecure communication channel. By employing quantum encryption, Alice can encode her message using a cryptographic key generated through QKD. This encoded message is then sent to Bob, who uses the corresponding decryption key to retrieve the original plaintext message. Even if an eavesdropper, commonly referred to as Eve, intercepts the encoded message, she would not be able to decipher it without the decryption key, ensuring the confidentiality of the communication.
Quantum encryption and decryption processes offer unparalleled security, making it extremely challenging for adversaries to break the encryption and gain access to sensitive information. By harnessing the fundamental principles of quantum mechanics, quantum cryptography opens up new frontiers in secure communication, paving the way for advancements in fields like cybersecurity, finance, and government intelligence.
Quantum secure communication networks
Quantum secure communication networks are a fascinating and cutting-edge area of study within the field of quantum cryptography. With the rise of advanced technologies, traditional encryption methods are facing increasing vulnerabilities, posing a significant threat to the security and privacy of sensitive information. This is where quantum secure communication networks come into play.
Unlike conventional encryption techniques that rely on mathematical algorithms, quantum secure communication networks leverage the principles of quantum mechanics to ensure unparalleled security. These networks utilize the unique properties of quantum particles, such as photons, to enable secure communication channels that are virtually impenetrable.
One of the most noteworthy examples of quantum secure communication networks is quantum key distribution (QKD). In QKD, the sender and receiver exchange quantum-encoded keys, which are generated using the properties of entangled particles. These keys are then used to encrypt and decrypt the data sent between the parties. The remarkable aspect of QKD lies in the fact that any attempt to intercept or eavesdrop on the communication would unavoidably disturb the quantum state of the particles, alerting the participants to the presence of an intruder.
Another promising application of quantum secure communication networks is quantum teleportation. While the name might evoke thoughts of science fiction, quantum teleportation is a real phenomenon in the realm of quantum mechanics. It involves the transfer of quantum information from one location to another without physically transmitting the particles themselves. This opens up possibilities for secure communication over long distances, as quantum information can be teleported between distant nodes in a quantum network.
The development of quantum secure communication networks holds immense potential for revolutionizing the field of cryptography. As technology continues to advance, it becomes imperative to adopt robust security measures that can withstand the threats posed by quantum computing and other emerging technologies. By exploring and harnessing the power of quantum mechanics, we can unlock the secrets of secure communication and pave the way for a future where information privacy is safeguarded at the quantum level.
Advantages and challenges of quantum cryptography
Quantum cryptography, also known as quantum key distribution (QKD), holds immense promise in revolutionizing the field of secure communications. As with any groundbreaking technology, it comes with its own set of advantages and challenges.
One of the key advantages of quantum cryptography lies in its unparalleled level of security. By harnessing the principles of quantum mechanics, it offers a level of encryption that is theoretically unbreakable. This is due to the inherent nature of quantum particles, which are extremely sensitive to any form of observation or interference. As a result, any attempt to intercept or eavesdrop on quantum encrypted messages would inevitably be detected, ensuring the confidentiality and integrity of the communication.
Additionally, quantum cryptography provides a unique feature called “quantum key distribution.” Unlike traditional cryptographic methods that require the exchange of a secret key over an insecure channel, QKD enables the distribution of cryptographic keys with absolute security. This is achieved by leveraging the principles of quantum entanglement or the properties of quantum particles to establish a shared secret key between two parties. This ensures that even if an adversary gains access to the communication channel, the intercepted key would be useless without being detected.
However, despite its undeniable advantages, quantum cryptography also faces several challenges. One of the significant obstacles is the fragile nature of quantum states. Quantum particles are highly susceptible to environmental disturbances, such as temperature fluctuations or electromagnetic interference. These disturbances can introduce errors into the transmitted information, leading to a decrease in the overall security of the system. Overcoming these challenges requires the development of robust and error-correcting quantum protocols, as well as the implementation of stringent measures to minimize environmental noise.
Another challenge lies in the practical implementation of quantum cryptographic systems. Currently, QKD systems are complex and expensive, often requiring specialized equipment and expertise. Scaling up these systems to be commercially viable and integrating them into existing communication networks pose technical and logistical challenges. However, ongoing research and advancements in quantum technologies aim to address these challenges, paving the way for more accessible and cost-effective quantum cryptographic solutions.
In conclusion, quantum cryptography offers unparalleled security and the potential to revolutionize secure communications. Its advantages in providing unbreakable encryption and secure key distribution make it a promising field of study. Although challenges exist, ongoing advancements and research in quantum technologies bring us closer to unlocking the full potential of quantum cryptography in the real world.
Quantum-resistant cryptography: Preparing for the future
As technology continues to advance at an unprecedented rate, it is crucial for us to anticipate the future challenges that may arise in the field of cryptography. With the rise of quantum computing, traditional cryptographic systems that rely on mathematical algorithms are becoming increasingly vulnerable to attacks. This calls for the development and implementation of quantum-resistant cryptography.
Quantum-resistant cryptography, also known as post-quantum cryptography, is a field of study that aims to create cryptographic systems that can withstand attacks from quantum computers. These systems are designed to be resistant to quantum algorithms that can break traditional encryption methods.
One of the most promising approaches in quantum-resistant cryptography is lattice-based cryptography. Lattice-based cryptography relies on the hardness of certain mathematical problems involving lattices, which are geometric structures formed by repeating patterns of points in a multi-dimensional space. These problems are believed to be difficult for both classical and quantum computers to solve.
Another approach is code-based cryptography, which is based on error-correcting codes. These codes introduce redundancy into the data, allowing errors to be detected and corrected. Code-based cryptography has been extensively studied and is considered to be a viable option for resisting quantum attacks.
Furthermore, there are other approaches being explored, such as multivariate cryptography, hash-based cryptography, and isogeny-based cryptography. Each of these approaches leverages different mathematical concepts to create cryptographic systems that are resistant to quantum attacks.
While quantum computers capable of breaking traditional cryptographic systems have not yet been fully realized, it is essential for organizations and individuals to start preparing for the future. This includes researching and implementing quantum-resistant cryptographic algorithms and protocols.
In conclusion, quantum-resistant cryptography is the key to ensuring the security of our digital infrastructure in the face of quantum computing advancements. By exploring various approaches and staying ahead of the curve, we can proactively protect sensitive information and maintain the confidentiality and integrity of data in the quantum era.
Applications and potential impact of quantum cryptography
Quantum cryptography, also known as quantum key distribution (QKD), holds immense potential in revolutionizing the field of secure communication. The applications of quantum cryptography extend beyond traditional encryption methods, offering unbreakable security and ensuring the privacy of sensitive information in various domains.
One of the most significant applications of quantum cryptography is in the realm of financial transactions. With the increasing reliance on digital transactions, protecting sensitive financial data from prying eyes is of paramount importance. Quantum cryptography provides a foolproof method of securing these transactions, eliminating the risk of data breaches and unauthorized access. By leveraging the principles of quantum mechanics, QKD allows for the secure exchange of cryptographic keys, ensuring that only authorized parties can decrypt the information.
Another field that can benefit greatly from quantum cryptography is government and military communications. Classified information and sensitive data are constantly at risk of interception and decryption by adversaries. Quantum encryption offers an unprecedented level of security, making it nearly impossible for hackers or eavesdroppers to decipher the transmitted data. This technology can safeguard critical government communications, ensuring the integrity and confidentiality of classified information.
The healthcare industry also stands to gain from the advancements in quantum cryptography. Patient data, medical records, and research findings are highly sensitive and must be protected to maintain patient privacy and prevent data breaches. Quantum cryptography provides a robust solution by safeguarding the transmission and storage of healthcare data, offering a secure environment for collaboration among healthcare professionals and researchers.
Furthermore, the impact of quantum cryptography extends to the realm of IoT (Internet of Things). As our world becomes increasingly interconnected, the need for secure communication between IoT devices becomes crucial. Quantum cryptography offers a solution to address the vulnerabilities present in conventional encryption methods, ensuring the confidentiality and integrity of data exchanged between IoT devices.
In conclusion, the applications and potential impact of quantum cryptography are vast and far-reaching. From securing financial transactions to protecting government communications, healthcare data, and IoT devices, quantum cryptography has the power to revolutionize the way we communicate and safeguard sensitive information. As this technology continues to evolve, we can expect to witness its widespread adoption across various industries, providing an unparalleled level of security in our digital age.
Current research and developments in quantum cryptography
Quantum cryptography, with its promises of unbreakable encryption and secure communication, continues to be an area of intense research and development. Scientists and researchers worldwide are delving deeper into this fascinating field, exploring new possibilities and pushing the boundaries of what is currently known.
One significant breakthrough in quantum cryptography is the concept of quantum key distribution (QKD). QKD enables the distribution of cryptographic keys through quantum channels, guaranteeing their security against any form of interception or tampering. This technology relies on the principles of quantum mechanics, such as the Heisenberg uncertainty principle and the no-cloning theorem, to ensure the secrecy of the keys.
Another area of active research is quantum-resistant cryptography. As quantum computers become more powerful, traditional encryption methods that rely on mathematical algorithms, such as RSA and AES, may become vulnerable to attacks. To counter this threat, researchers are developing new cryptographic protocols that can withstand the computational power of quantum computers. These post-quantum cryptography algorithms aim to provide long-term security for sensitive data and communications.
Furthermore, scientists are exploring the potential of quantum teleportation in cryptography. Quantum teleportation allows the transfer of quantum information from one location to another instantaneously, without physically transmitting the information through a medium. This phenomenon could revolutionize secure communication by enabling the transfer of encryption keys over long distances, immune to interception.
In addition to these developments, quantum cryptography is also being applied to other fields, such as secure quantum voting systems and quantum blockchain technology. These applications leverage the unique properties of quantum mechanics to ensure the integrity and confidentiality of data, making them highly resistant to manipulation or hacking.
As the field of quantum cryptography continues to advance, we can expect even more exciting breakthroughs and practical implementations in the near future. These developments hold the potential to revolutionize the way we secure our communications, protect sensitive information, and safeguard our digital world from emerging threats. Quantum cryptography is indeed an intriguing realm that promises to unlock a new era of secure and private communication.
Conclusion: Embracing the future of secure communication with quantum cryptography
In conclusion, quantum cryptography presents a revolutionary approach to secure communication that holds tremendous potential for the future. As we have explored in this article, the principles of quantum mechanics provide a solid foundation for developing unbreakable encryption methods.
By harnessing the unique properties of quantum particles, such as superposition and entanglement, quantum cryptography offers a level of security that surpasses traditional cryptographic methods. It enables the creation of encryption keys that are virtually impossible to intercept or decipher, ensuring the confidentiality and integrity of sensitive information.
Real-life examples, such as quantum key distribution (QKD) networks and quantum-resistant algorithms, have shown promising results in various fields, including government communications, financial institutions, and healthcare systems. These applications demonstrate the practicality and viability of quantum cryptography in safeguarding digital communication against ever-evolving threats.
As we embrace the future, it is crucial for researchers, scientists, and policymakers to continue exploring and advancing quantum cryptography. By investing in research and development, we can further enhance the efficiency, scalability, and accessibility of quantum cryptographic systems.
However, it is important to note that the implementation of quantum cryptography on a large scale is still in its early stages. There are challenges to overcome, such as the need for robust and reliable quantum hardware, as well as the integration of quantum protocols into existing communication infrastructure. Nonetheless, the progress made thus far is highly promising and paves the way for a new era of secure communication.
In conclusion, quantum cryptography has the potential to revolutionize the way we communicate, offering unparalleled security and privacy in the digital age. By embracing this cutting-edge technology, we can ensure that our sensitive information remains protected from malicious attacks, empowering individuals and organizations to operate in a trusted and secure environment. Let us embrace the future of secure communication with quantum cryptography and unlock the secrets it holds.
We hope this blog post has shed some light on the intriguing world of quantum cryptography. Through real-life examples, we have shown how this cutting-edge technology can revolutionize the way we secure our data and communications. From quantum key distribution to quantum-resistant algorithms, the possibilities are truly fascinating. As we continue to explore and understand the potential of quantum cryptography, we can look forward to a future where our information is protected on an unbreakable level. Keep exploring, keep innovating, and stay tuned for more exciting developments in the field of quantum cryptography!
——————————


